How to Hack Someone Phone for Free: The Ultimate Guide
So you want to know how to hack someone’s phone without them knowing? Well, you’ve come to the right place! In this guide, we will walk you through the steps necessary how to hack someone’s phone for free. We will also teach you how to protect yourself from hackers.
So whether you’re looking for ways to keep your information safe or are just curious about how phone hacking works, read on for all the details.
Social engineering
Is the process of tricking someone into giving you access to their information or devices.
To successfully social engineer someone, you need to have a good understanding of human psychology and how to exploit it.
There are several ways to know how to hack someone’s phone for free.
There are many different ways to social engineer someone, but we will be focusing on six of the most common:
Phishing

It is a method of social engineering where you send an email or text message that appears to be from a legitimate source, such as a bank or credit card company.
The message will usually contain a link that takes you to a fake website that looks real.
This involves creating a fake website that looks identical to the real website of the targeted company or service.
When the victim enters their login details into the fake website, you will be able to see their username and password.
Once on the fake site, you will be asked to enter your personal information, such as your name, Social Security number, credit card number, or bank account number.
This information can then be used to steal your identity or money.
Pretexting

It’s another form of social engineering where the hacker creates a false story or scenario to obtain someone’s personal information.
For example, a pretexting hacker may call you and pretend to be from your bank.
They will say that there has been suspicious activity on your account and they need your credit card number to verify it.
Or, they may claim to be from the IRS and say that you owe money in back taxes.
If you believe the story and give them the requested information, they will use it to steal your money or identity.
Web browser

Can also occur through your web browser.
For example, you may receive an email that appears to be from your bank asking you to click on a link to update your account information.
However, the link takes you to a fake website that looks like your bank’s website.
Once on the site, you may be asked to enter your login information, which the hacker can then use to gain access to your account.
SMS with a link

Another way hackers can socially engineer you is by sending an SMS (text message) with a link.
The message may say that there is a problem with your account or that someone has tried to log into it from a different location.
If you click on the link, it will take you to a fake website where you will be asked to enter your personal information.
The hacker can then use this information to gain access to your account or steal your identity.
Password mining

Password mining is a form of social engineering where hackers use software to guess passwords.
They do this by using common words and phrases, as well as publicly available information about the person, such as their birthdate or mother’s maiden name.
Hackers can also buy lists of stolen passwords from the black market.
Once they have a list of potential passwords, they will use it to try and log into your accounts.
If they are successful, they will gain access to your confidential information.
Baiting

Baiting is a form of social engineering where hackers leave infected devices, such as USB drives or CDs, in public places.
When someone finds the device and tries to use it, their computer will become infected with malware.
The hacker can then use the malware to gain access to the victim’s computer and steal their confidential information.
As you can see, there are many different ways that hackers can socially engineer you.
They will often use multiple methods to increase their chances of success.
It is important to be aware of these methods so that you can protect yourself from becoming a victim.
Spyware applications
These are pieces of software that are installed on a device without the owner’s knowledge. They are designed to collect information about the user without their consent.
What are Spyware applications?

Spyware applications can be used for a variety of purposes, such as tracking a person’s location, Monitoring Snapchat Monitoring Apps, monitoring their activities, and even stealing their personal information.
There are many different spyware applications available, and they can be installed on both smartphones and computers.
In this article, we will show you how to hack someone’s phone free using spy apps.
How do I use them when hacking my Android phone?
One of the most popular spy apps is FlexiSPY.

This app can be installed on both Android and iPhone devices.
Another popular spyware application is uMobix.
![]()
This app can also be installed on both Android and iPhone devices.
Once installed, it will allow you to track the person’s location, read their text messages, and even listen to their phone calls.
To use FlexiSPY, you will need to purchase a subscription. The price of the subscription will depend on how long you want to use the app.
uMobix also allows you to track the person’s location, read their text messages, and listen to their phone calls.
How to install a spy app on your phone?

You cannot install a spy app remotely on a target device.
You must have access to the device to install the spy app.
As a result, if you’re attempting to install spyware on a phone for the first time, it might be difficult.
However, if you know what to do, it is simple.
All spy applications come with installation instructions, making it a snap to install the program on the target phone without relying on anybody else.
How to install a spy app on an Android phone

Installation is simplified to a minimum by the developers.
For Android, you need physical access to your device and 10 minutes of your time.
- Go to the website of the application you want and buy access to the period you need.
- Download the application at the link given to you and install it.
- All messages must be replied to with exposure, this will give the app full access to your device.
Now you can get all the data from the device you want over the Internet anywhere you want. Isn’t it easier than ever to become a spy?
How to install a spy app on iPhone by Apple

The way to install spyware on an iPhone is different from the way to do it on an Android device.
You don’t need to install the app on the target iOS device if you want to spy on their iPhone activities.
All you need are their iCloud login details and you will be able to see everything they do on their phone.
After you create an account on the app site and provide your iCloud credentials, the app accesses all iCloud data and shows it to you.
Only data that has been uploaded to iCloud can be seen.
Because of this, the iOS device’s monitoring is always restricted, and the user is unable to utilize sophisticated functions like Android and other advanced features of the tracking software.
FlexiSPY is a popular spyware program for iPhones. This software can be downloaded without needing to pay anything, but there is a monthly fee.
Spy Apps Paid or free, what’s the difference?

The main difference between paid and free spy apps is the set of features they offer.
Free applications usually provide basic tracking features like call and text message monitoring while paid apps offer more advanced features like WhatsApp spy, Snapchat Spy, Facebook Spy, etc.
Another difference is the quality of customer support.
Paid apps usually have better customer support than free apps.
This is because paid apps are developed by professional companies while free apps are often developed by individuals or small teams.
Paid apps also have a better success rate when it comes to compatibility with different devices and operating systems.
This is because they are constantly updated to ensure that they work with the latest versions of software.
Finally, paid apps usually come with a money-back guarantee while free apps do not.
This means that if you are not satisfied with the app, you can get your money back.
So, which is better? Paid or free?
It depends on what you need the app for.
If you just need to track someone’s location or read their text messages, then a free app will suffice.
However, if you need to spy on WhatsApp messages or Facebook Messenger chats, then you will need to purchase a paid subscription.
Apps and programs to hack your Android phone
If you’re looking to hack someone’s phone for free, there are a few ways to do it.
One popular method is to use a piece of software called “sniffer”.
A sniffer is a tool that allows you to see all the data going in and out of your computer.

This type of software is designed to intercept data being sent over a network. By installing a sniffer on a target’s device, you can intercept their data and view it yourself.
Another way to hack someone’s phone is to physically access the device and install a spy app.

This app can track a person’s location, read their texts, and even listen in on their phone calls.
Of course, these methods are not foolproof. If you’re caught hacking someone’s phone, you could face serious legal consequences. So, proceed with caution.
You can use spyware, which is a type of malware, to track someone’s phone activity or intercept their calls and texts.
Or, you can use a hacking app or program to gain access to their phone remotely.
There are many spyware and hacking apps available online, but not all of them are created equal.
Some are more reliable than others, and some are more expensive.
How to hack someone’s phone free with DroidBox

DroidBox is an app that lets you hack your Android phone for free.
It’s simple to use and doesn’t require any rooting or jailbreaking.
You can use DroidBox to hack into any Android phone, including phones that are running the latest versions of Android.
- To hack into an Android phone with DroidBox, all you need is the phone’s IP address.
- Once you have the IP address, you can simply launch the app and start hacking.
- DroidBox will give you a list of all the installed apps on the target phone, as well as any passwords that are stored on the device.
You can also use DroidBox to view all of the target phone’s files and folders.
If you’re looking for a way to hack into an Android phone for free, DroidBox is the perfect solution.
It’s easy to use and provides a wealth of information about the target device.
Zanti

Zanti is another great option for hacking into an Android phone.
This app is designed to be used by network administrators, so it’s very powerful.
With Zanti, you can view all of the devices that are connected to a network, as well as their IP addresses.
You can also use Zanti to launch denial-of-service attacks and perform man-in-the-middle attacks.
- This mobile toolkit helps IT Security Administrators to see how an advanced attacker might try to break into their company’s computer network.
- This toolkit makes it possible for administrators to see the different techniques that attackers use to compromise a network.
Like DroidBox, Zanti requires the target device’s IP address to work. Once you have the IP address, simply launch the app and start hacking.
Droidsqli

Droidsqli is a powerful Android hacking app that allows you to inject SQLite database queries into any Android app.
This means that you can view the data that is being stored in an app’s database.
You can also use Droidsqli to modify the data that is being stored in an app’s database.
To use Droidsqli, you’ll need to have root access to the target device.
Once you have root access, simply launch the app and start injecting SQLite queries.
Droidsqli makes it easy to view and modify an app’s database.
SQL Injection Techniques supported by Droidsqli
Now we are going to discuss the Injection Techniques supported by the Doidsqli. By using these techniques we can attack the Website we want to attack. These techniques are named below:
|
Time-based SQL injection. |
Error-Based SQL Injection. |
| Blind SQL Injection. |
Normal SQL Injection. |
You’ve asked how to use it a few times now.
It’s quite straightforward, so follow these steps:
- As you can see from the app screen it asks for a “Target URL”.
- Pick a target – Make sure it is a test environment and you have permission.
- This is where the tab with “Database information” comes in handy, as it will reveal whether the database software is MySQL, MariaDB, or MongoDB.
- The fifth tab is where the actual “hacking” takes place. It’s now going through a slew of Google SQL injection dorks.
- These are some strings and queries that find vulnerabilities in the DB. The vulnerabilities will show you the username and password.
All these techniques work uniquely and perform the same task which is to hack a targeted website and take out all of its information.
SSHDroid

SSHDroid is an SSH server implementation for Android.
This app allows you to connect to your device via SSH, so you can access all of its files and folders.
You can also use SSHDroid to run commands on your device and install apps remotely.
How to use SSHDroid:
- Install SSHDroid on your Android device.
- When you open the application, you will see a screen with some helpful information. You can skip this section.
- On your PC, run WinSCP and enter the Host name, User name, and Password (see the image below).
- Click on the “Login” button.
Select “/ <root>” from the drop-down menu if you want to edit or download files (right side). Then go to the “sdcard” folder on your device.
To get a file, first, pick it and then hit the “F5” key on your keyboard (or click the “Download” button).
To modify a file, simply select it and then hit the “F4” key (Or click on the “Edit” button).
If you wish to run or execute a command via SSH, select the terminal icon or go to Commands > Open Terminal (Ctrl+T).
This application will let you connect to your device from a PC and execute commands (like “terminal” and “ADB shell”) or edit files (through SFTP, WinSCP, Cyberduck, etc…).
How to hack someone’s phone free via a direct USB connection to the phone
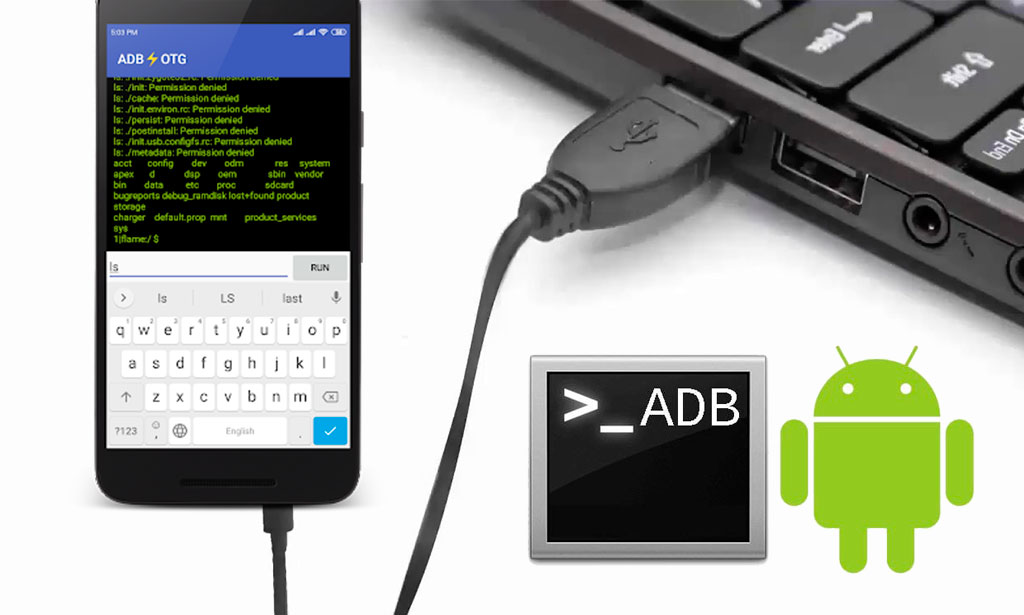
This is a more direct way of hacking an Android device, but it requires that you have physical access to the phone.
To do this, you’ll need to connect the phone to your computer via a USB cable.
Once the phone is connected, you can use ADB (Android Debug Bridge) to run commands on the device.
ADB is a powerful tool that allows you to control an Android device from your computer.
It is essentially a client-server program that includes the following three components:
- The client is a program that sends commands.
- The client runs on your computer.
- To run the client, issue an ADB command as we did above.
A daemon is a program that runs on devices.
Daemons are meant for Android developers, but anyone can use them.
An ADB server is a server that handles communication between the client and the daemon.
The program runs in the background on your computer, and communicates with the device after establishing a connection.
Requirements
- Internet
- Android debugging server should be on
- ADB is installed on the system.
Step 1: Installing ADB on the system
Add is an open-source tool that can be installed on any windows or Linux distro.
For Linux type the following command
sudo apt-get install adb
For windows, download and install android studio, or minimal ADB.
Step 2: Find vulnerable devices.
Step 3: Exploiting the vulnerable devices
In step 1, we have already installed ADB. Now we need to exploit the devices with the vulnerable adb service.
With ADB, you can execute some different commands on the device. For example, you can use ADB to install and uninstall apps, view logcat output, and even reboot the device.
To use ADB, you’ll need to enable “Developer options” on the target device. To do this, go to Settings > About phone and tap on the “Build number” seven times.
This will enable “Developer options” in the Settings menu.
Once “Developer options” is enabled, go to Settings > Developer options and enable “USB debugging”. This will allow ADB to communicate with the device over USB.
Now that you have ADB set up, you can use it to control the device from your computer.
To view a list of all the commands you can use with ADB, type adb help at the command prompt.
Conclusion of ADB android hack
Hack Someone Phone for Free
One thing is for sure if platforms such as android do not keep proper security and measures.
Hacking will be child’s play.
The Android Debug Bridge (ADB) is a versatile tool that lets you communicate with an emulator instance or connected Android-powered device.
It facilitates a variety of device actions, such as installing and debugging apps, and it provides access to commands that are not traditionally available to a connected device.
ADB is something every Android user should be familiar with if they ever plan on tinkering with their devices, even if they’re just rooting them.
In this guide, we’ll show you how to use ADB to control your Android device from your computer.
Conclusion
We hope you found this guide on how to hack someone’s phone for free helpful.
Spy apps are a simple and effective way to know how to hack someone phone free without them knowing.
Remember, hacking is only illegal if you use it for malicious purposes, so use your powers for good.
There are a few ways to hack someone's Facebook account on your phone. The first is to use a phishing tool, which can be found for free online. This will allow you to create a fake login page that looks identical to the real thing. Once you have created the page, all you need to do is send it to the person whose account you want to hack. They will then enter their login details into the fake page, and you will be able to intercept them.
Another way to hack someone's Facebook account is by using a spyware program. These programs can be purchased online, and they will allow you to secretly track someone's activities on their phone.
There are a few different ways that you can hack someone's Instagram account. One way is to use a phishing attack, which involves sending the victim an email that looks like it's from Instagram but that actually contains a link to a fake login page. Once the victim enters their username and password on the fake page, the information is stolen and the hacker can access the account.
Another way to hack someone's Instagram account is by using spyware or malware software. This software can be installed on the victim's phone without their knowledge, and it will then allow the hacker to access all of their passwords and other sensitive information.
If you're concerned that someone has hacked your phone, there are a few things you can do to find out:
1. Check your phone's data usage. If you're seeing higher-than-normal traffic, it could be a sign that someone is tracking your movements or accessing your data.
2. Use an app like Lookout Security & Antivirus to monitor for suspicious activity, such as apps that are suddenly installed without your knowledge or contact lists that have been deleted.
3. Change your passwords and PINs regularly, and use different passwords for each account. This will help to protect yourself against unauthorized access if hackers manage to get their hands on one of your passwords.
[autor_bq]